This is coolbert: What Craig is talking about with regard to American radio insecurity is the adoption by American military forces world-wide of the automated CEOI [communications electronic operating instructions]. A response to the realization that American radio procedures were inadequate and had become an absolute liability. Too much valuable and potentially very damaging intelligence was being developed by the enemy who was able to intercept and analyze American radio traffic.
Something had to be done. And something was. This was the automated CEOI.
I like to refer to the automated CEOI as the "OH MY GOD" book. That is what the average soldiers reaction is when you see it. A thick document that at initial appearance is intimidating. But it must be used, is used, and is a tremendous improvement over what existed before. [Only a small portion of the CEOI is actually germane to any given day of a units radio usage. First glance intimidation of the CEOI is somewhat deceiving].
With the automated CEOI, all callsigns, suffixes, frequency usage, etc., have become uniform throughout the U.S. military. And change on a daily basis. A LOT of thought was given to the automation system for generating and assigning the callsigns, the suffixes [The suffixes identify an individual transmitter being used within a unit. I.e., the suffix 09 would mean the transmitter of the unit commander, 16 the transmitter of the executive officer, etc.], and the frequency usage. Duplications, contradictions, and conflicts have been avoided with the automated system. Given the large number of radio transmitters existing with say an American infantry division [as many as 10,000 [?????]], this is no small task.
Authentication/challenge/reply is also provided for within the automated CEOI by a daily changing key system facilitated by the use of a small, simple clipboard device [KAL-61] that has a slide mechanism on it. This daily changing key system allows for challenge/reply, encryption of map coordinates, and a simple speller code.
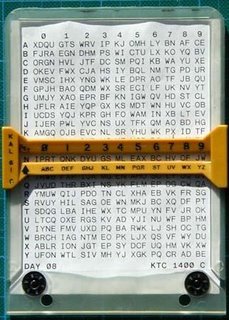
The automated CEOI also provides a two-part operational ["OP"] code to send and receive encoded messages, regardless of whether a unit has working secure cryptographic equipment or not. These OP codes also change on a regular basis [once every two days] and provide a pretty good degree of security if used judiciously. Your opposition would have to intercept a lot of radio traffic using the op codes. And then the process of reading the secret encoded traffic would take some time. What intelligence that could be gleaned by reading the messages, if they could be read, would be minimal as the information would be out of date by the time the traffic was read.
This automated CEOI IS hard to use unless a radio operator is skilled at using it. And not all radio operators are. But if people are trained and practiced in the use of the automated CEOI, they cannot go wrong and will not have to worry about providing intelligence to the enemy by using antiquated and poorly constructed systems of callsigns, frequencies, and codes and ciphers.
Poor use of radio communications can be a tremendous liability to any military. The automated CEOI was a quantum leap forward for the U.S. military.
[It may be that the current families of spread-spectrum technology, frequency hopping transmitters and receivers [the new 900 MHZ and greater cordless phones are an example of this technology] and built in cryptographic capability has rendered the ability of the enemy to glean intelligence from the intercepts of U.S. radio communications null and void. At least for a time?? But I would not rule out the possibility that this is NOT the case, or always will be the case. Radios must be used judiciously. They were not in Vietnam, with disastrous results in some cases]
coolbert.

0 Comments:
Post a Comment
Subscribe to Post Comments [Atom]
<< Home